MuleSoft Technical Guides

Isolate your CloudHub worker instances using VPN
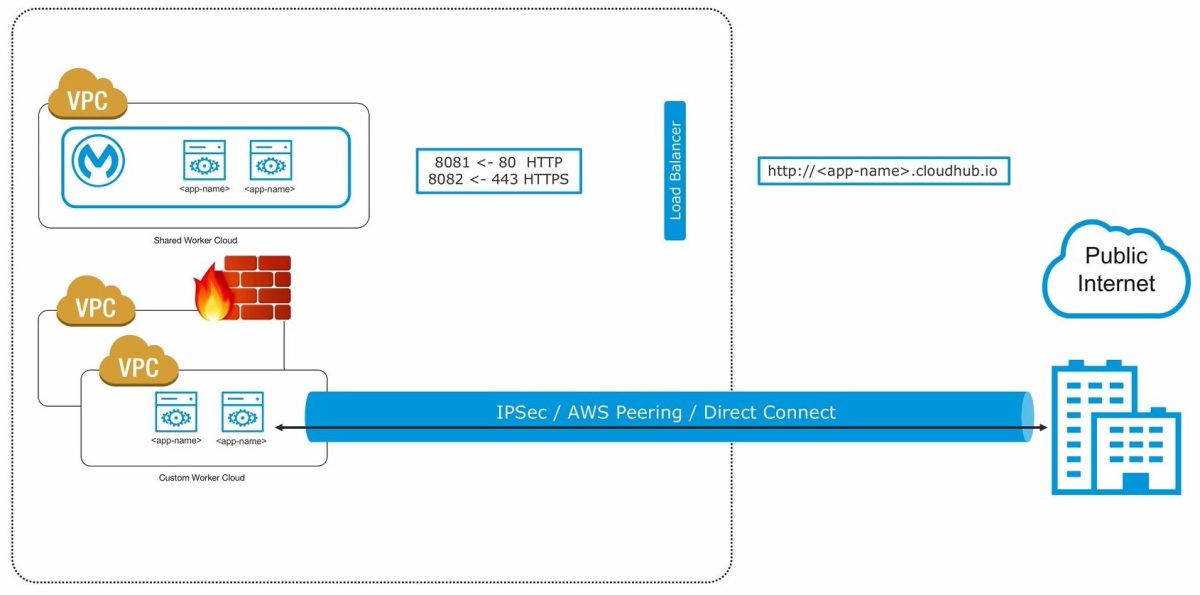
MuleSoft CloudHub – A multi-tenant integration platform as a service. Applications hosted on CloudHub workers or instances are balanced by a shared load balancer provided by MuleSoft. At every given point of time, your MuleSoft API deployed on CloudHub might want to interact with the on-premise resources, and for that, we need to have a secured connection tunnel that is not exposed on the public cloud. The article will help you isolate CloudHub worker using VPN.
Anypoint VPC (Virtual Private Cloud)
Anypoint VPC (Virtual Private Cloud) allows you to create a private coherent and secluded network to host your mule applications. VPC allows to connect CloudHub workers to your corporate data center using the below techniques:
· IPSec Tunneling (Secure VPN Tunnel)
· AWS Peering
· AWS Direct Connect
Lets take a look at the advantages, characteristics, and configurations of Anypoint VPCs.
Advantages of MuleSoft Anypoint VPC
· Connect CloudHub to any private cloud or on-premise data center.
· Create a mesh of secure virtual networks within CloudHub.
· Secure your worker instances.
Points to remember while configuring Anypoint VPC
· Ensure you create the VPC in the same region or near your data center or AWS region (VPC Peering).
· Generally the setup has one isolated network for your production environment and another for non-production environments like dev, test, UAT.
· Multiple deployment environments can be mapped to the same VPCs.
· Always create the VPC in the parent business group and share amongst sub-business groups.
Creating a VPC- Virtual Private Cloud
Creating a VPC is not a hard and fast process and can be done in a couple of minutes.
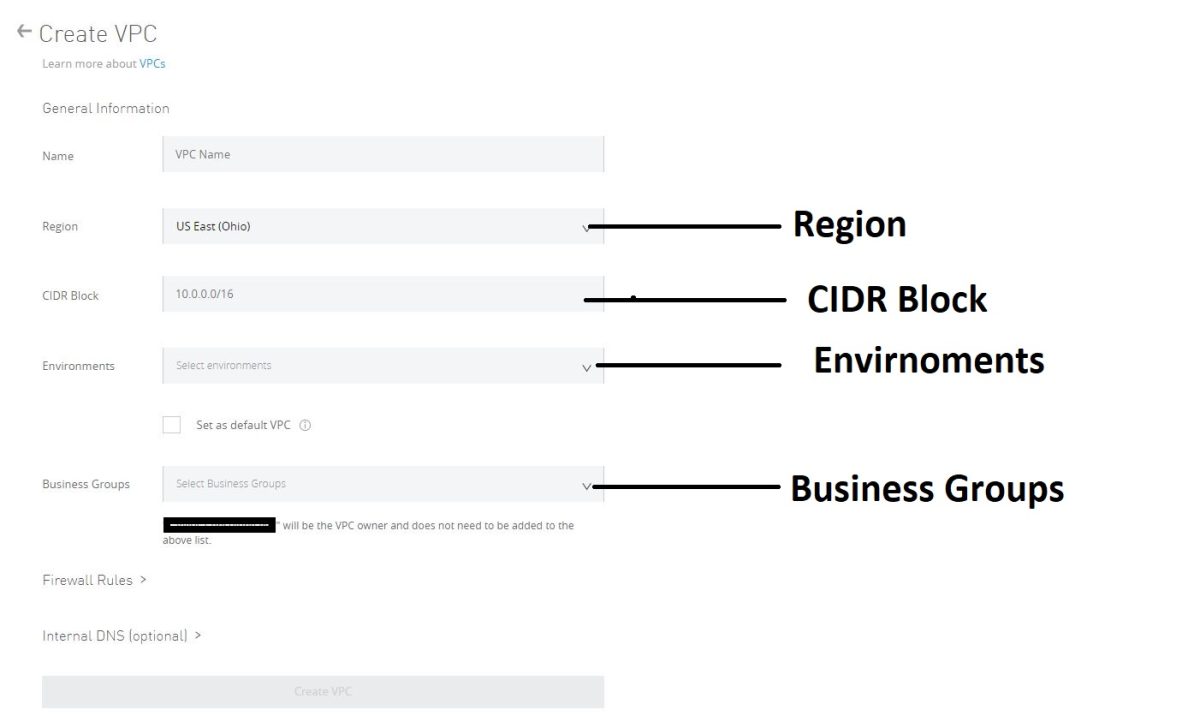
You need to provide the values of four parameters viz.
· Region
· CIDR block
· Environments
· Business groups
VPC Region
VPC region is selected from a cluster of available regions. However, MuleSoft’s recommendation to choose a region may vary depending upon how the connectivity follows your Anypoint VPC.
If the connection is private AWS peering, you need to create your Anypoint VPC in the same region as AWS. However, if it connects to your on-premises data center, you might have to pick a VPC region closest to your data center.
CIDR Block
The most important part of the configuration CIDR (Classless Inter-Domain Routing) block can be calculated by exponential notation 2N ranging from 28 – 216. /24 is the smallest network subnet block that can be assigned for Anypoint VPC. (Total 256 IP Addresses), on the other side, the largest subnet can be /16 (provides 65,536 IP Addresses). It is important to size your VPC large enough to accumulate enough IP addresses to support zero application downtime.
While choosing an IP range, consult your Data Center Infra team to not conflict with the address space being used at the Data Center.
Considering two IPs for each worker instance to support zero-downtime deployments. MuleSoft recommended that sizing is to 10X your maximum number of expected apps to deploy per environment in the VPC.
Environments
You can choose multiple environments for each VPC, while the configuration is based upon the type of deployment. e.g., SIT, UAT, Test can be pointed to one VPC, and PROD can be pointed to another VPC.
Multiple environments can be picked for each VPC while configuration, based upon the type of deployment,
If an environment is not selected, all applications deployed to the selected region will be associated with this Anypoint VPC.
NB: Don’t associate Anypoint VPC with a design environment. Apps can be deployed to the design environment only from Design Center and not from Runtime Manager.
Incorporating Business Groups within VPC
A VPC can be shared amongst various business groups within your organization. Therefore, MuleSoft recommends VPC should be created in the parent organization.
Anypoint VPCs are only vertically shared, i.e., A VPC can be shared to one of its business groups or can be shared from a business group to one of its child business groups.
Once shared, the reconfiguration of VPC, like changing the region, the environment, can be done by admins of associated business groups. In this case, the previous configuration is overwritten by the newly requested VPC configuration.
Creating firewall rules
When the Anypoint VPC is created, by default, four firewall rules are set. The practices can be reviewed and modified as per your requirements.
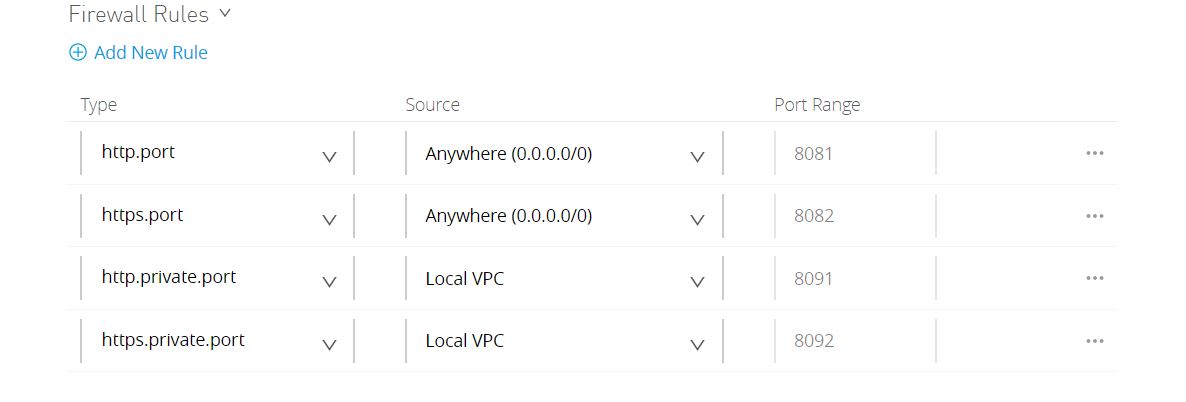
8081 and 8082 are listening to inbound traffic from anywhere to the VPC network. These are the default incoming HTTP and HTTPS port for requests to reach the CloudHub workers. They are by default configured while VPC uses MuleSoft’s shared load balancer, although they can be depreciated if you do not want isolated workers to be reached by public IPs.
8091 and 8092 ports are reserved by default for inbound connections within your local Anypoint VPCs. All within the organization and even CloudHub-dedicated LB allows you to access your workers using these IPs HTTP private port (8091) and HTTPS private port (8092).
You can open additional ports using firewall rules within your VPC, by clicking Add New Rule.
This article gives you insights to kick-off the configuration of your Anypoint VPC for safeguarding your CloudHub worker instances by creating required firewall rules and giving possible flexibility of connecting to internal on-premises or cloud assets.
Thanks for reading. Hopefully this will help all of you MuleSoft Developers to Isolate CloudHub Worker using VPN.